Featured
Table of Contents
- – Common Vpn And Tunneling Protocols
- – Common Vpn And Tunneling Protocols
- – Point-to-point Tunneling Protocol (Pptp)
- – What Are The Benefits Of Using Vpn Encryption?
- – How A Vpn (Virtual Private Network) Works - H...
- – Top Vpn Protocols Explained (+ Which Ones Yo...
- – What Is A Vpn? Types Of Vpns And How They Work
- – Vpn Tunnel: What It Is And How It Works
- – What Is A Vpn Tunnel
- – [Solved] Before You Begin
Common Vpn And Tunneling Protocols
This offers more versatility than producing an SSH tunnel to a single port as formerly described. SOCKS can release the user from the constraints of linking only to a predefined remote port and server. If an application does not support SOCKS, a proxifier can be utilized to redirect the application to the local SOCKS proxy server.
In recent versions of Open, SSH it is even enabled to create layer 2 or layer 3 tunnels if both ends have made it possible for such tunneling abilities. This develops tun (layer 3, default) or tap (layer 2) virtual user interfaces on both ends of the connection. This enables regular network management and routing to be utilized, and when used on routers, the traffic for an entire subnetwork can be tunneled.
Common Vpn And Tunneling Protocols
VPNs can deal with any device that links to the web and can run a VPN app, including your smart device, computer system, and some wise Televisions. All you need to do is download a VPN app to your device and follow the guidelines to link to a VPN server. When you connect to the VPN server, an encrypted connection is worked out in between your gadget and the VPN server.
(Note: Sites can perform other kinds of tracking, so you must likewise be sure to utilize a personal web browser and take care about the information you actively send to any website.) In the last 20 years, mass surveillance has been released versus entire populations in lots of countries. This consists of the assessment of information packages as they travel across the internet.
Point-to-point Tunneling Protocol (Pptp)
This leaves your traffic susceptible to interception, including any passwords or other sensitive data you go into. A larger issue is that the data gathered from you by any of the above trackers will suffer an information leakage that exposes your information. A VPN will not prevent all (and even most) leakages, but it is another layer of defense in an information area developed to extract your information.
For example, lots of streaming websites are not accessible in certain nations. If you're taking a trip abroad, you can link to a VPN server back home to log in to your account. Proton VPN users can access many popular streaming websites by connecting to a Plus server in that country. There are other advantages of a VPN that are really important in certain use cases: Avoid peers from seeing your genuine IP address when utilizing P2P file sharing (Bit, Gush).
What Are The Benefits Of Using Vpn Encryption?
VPN protocols have different strengths and weak points. Here's a fast summary: An older VPN procedure with a number of known vulnerabilities.
Layer two tunneling protocol (L2TP) and Internet Protocol security (IPSec) are 2 procedures that frequently collaborate to work out the server connection and handle the file encryption, respectively. This is a more secure system than PPTP, but it may have vulnerabilities and typically isn't as quick or steady as newer procedures.
How A Vpn (Virtual Private Network) Works - Howstuffworks
A VPN tunnel is simply a metaphor for the encryption a VPN uses to conceal your information as it travels in between your gadget and the VPN server. The majority of web traffic shows up to others on the network, so 3rd parties, like your internet service provider or federal government companies, can see what websites you go to and where you are situated.
VPN tunneling also avoids hackers from misusing data by encrypting them from end to end. Most VPNs utilize AES-256 encryption, which armed forces, banks, and federal governments use to secure private information. It is technically difficult to break the AES-256 file encryption without a cipher key, as it would take trillions of years to do so.
Top Vpn Protocols Explained (+ Which Ones You Should ...
Like IKe, V2, Open, VPN uses formidable speed and security for VPN tunneling. It is likewise open source, which means experts have continually vetted and enhanced the procedure over the years. Wire, Guard is the most recent and most safe VPN encryption protocol. Compared to Open, VPN and IKEv2, Wireguard is much faster and more protected, thanks to its smaller code size.
Proxies just work for internet browsers and not apps. If you utilize an app in spite of connecting to the proxy, your actual IP address will still be exposed.
What Is A Vpn? Types Of Vpns And How They Work

VPN technology is not complex, however there are. All of this can get extremely technical, so here's a fast rundown of which types of VPN and tunneling procedures are best for your service.
It becomes active only when the user enables it. Otherwise, it doesn't have a permanent link. Organizations mainly utilize this type to. You can believe of it as a VPN connection making a safe and secure path from your gadget to access delicate documents or business materials on the other end.
Vpn Tunnel: What It Is And How It Works
A lot of organizations embrace generally hosted somewhere else, utilizing enormous data. Setting remote gain access to VPN up may not be the most practical option as in those cases, the information would be going from users' device to the main hub, to the information center and back. So not just this could present.
It's worth noting that you should plan depending on the number of users accessing them. The more of them you'll have, the more capable hardware you'll require. is to create a unified network that is always on. It requires separately configuring for both networks, and it works best for cases when you have numerous remote websites.
What Is A Vpn Tunnel
It offers detailed guidelines on product packaging the data and what checks to carry out when it reaches its location. These various methods. Here are the most popular ones. is a VPN tunneling protocol that secures data exchange by. It is twofold encryption the encrypted message sits in the information package, which is more encrypted once again.
: remote access or site-to-site. It ought to narrow down your list of alternatives. It's worth noting that neither remote access nor site-to-site are the only possibilities to set up an Internet-based VPN.
[Solved] Before You Begin
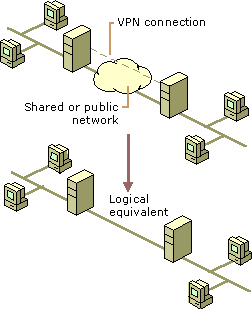
I.e., if you're currently using routers that natively support Open, VPN, it might make more sense to utilize them instead of tossing them out to get ones that can deal with Wireguard.
What is a VPN Tunnel & How VPN Tunneling Functions? Data, Prot is supported by its audience. As we search the internet, we leave crumbs of browsing data on the pages we check out.
Table of Contents
- – Common Vpn And Tunneling Protocols
- – Common Vpn And Tunneling Protocols
- – Point-to-point Tunneling Protocol (Pptp)
- – What Are The Benefits Of Using Vpn Encryption?
- – How A Vpn (Virtual Private Network) Works - H...
- – Top Vpn Protocols Explained (+ Which Ones Yo...
- – What Is A Vpn? Types Of Vpns And How They Work
- – Vpn Tunnel: What It Is And How It Works
- – What Is A Vpn Tunnel
- – [Solved] Before You Begin
Latest Posts
What Is A Business Vpn? Understand Its Uses And ...
5 Best Business Vpns In 2023 - Most Secure And Reliable
Best Business Vpn Options In 2023 [Keeping Smb Data ...
More
Latest Posts
What Is A Business Vpn? Understand Its Uses And ...
5 Best Business Vpns In 2023 - Most Secure And Reliable
Best Business Vpn Options In 2023 [Keeping Smb Data ...